


What is Trident?
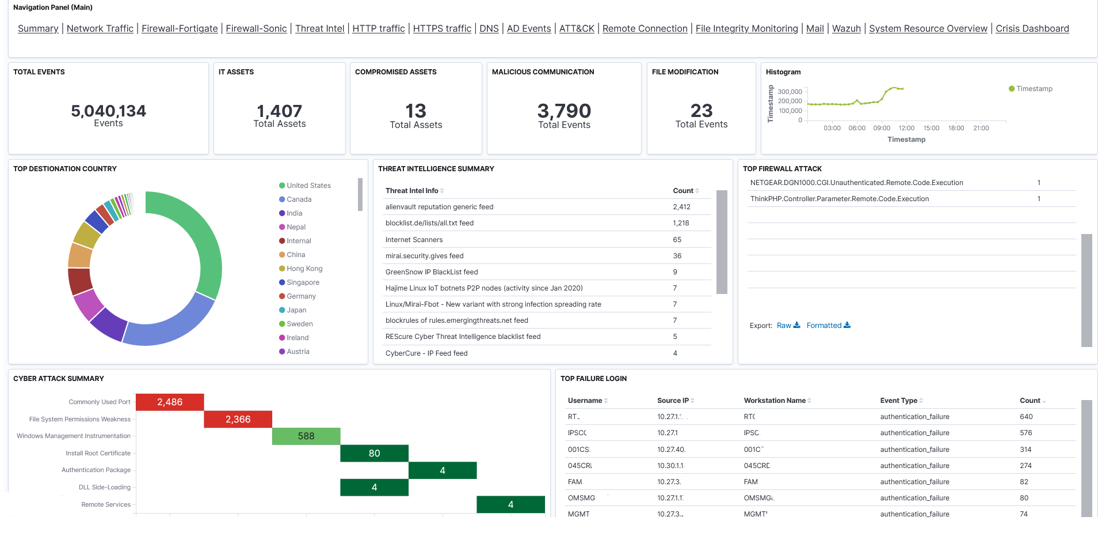
Vairav Trident is an AI enabled SIEM solution proffered by Vairav, consisting of built-in detection capabilities and integrated threat intelligence, that unleashes security visibility on entire threats that affect the network, providing the ideal mitigation method 24/7, 365 days a year .
Vairav provides 14 essential security capabilities to assist the management of compliance
and threats respectively.

Log Management
Vairav CTMS ingests structured and unstructured format of logs, normalizing them to a simplified form to retain both processed logs and raw logs as per the defined timescale ofthe customer.

Asset Inventory
This module is responsible for gathering the hardware inventory details such as Operating System, Network Interfaces, installed packages, ports status and the processes that are running in the assets.

Threat & Risk Detection
This module detects threats and risks within the customer’s organization, with the help of various security technologies such as Network IDS, Host IDS and security configuration assessment.

Anomaly Detection
This module is responsible for the identification of suspicious/unusual events that deviate from standard, normal, or expected events.

Correlation Engine
This module helps to identify the sequence of events that would indicate anomalies to detect a security incident. Furthermore, it correlates the events/logs from different sources, matches with the rules provided, triggering an alert whenever the conditions match.

AI-Enabled Threat Detection
It is an AI based threat hunting mechanism that uses trained AI modules to detect advanced malware techniques such as DNS Tunneling, DGA Detection and Malware Beaconing.

Vairav Threat Intelligence
Vairav CTMS uses Vairav Technology’s own threat intelligence server to collect information about IOCs and different campaigns running around the world, detecting the malicious communications in the network. Also, Vairav Threat Intelligence collects intelligence reports from more than 110 threat feeds on a daily basis.

Vulnerability Assessment
This module detects the vulnerable systems, software/applications, or devices within the network to provide remediation/mitigation processes to the vulnerabilities. On the contrary, attackers may use the vulnerabilities to bypass and compromise the system ultimately.

Incident Response
This module keeps records of all the incidents raised by the SOC team, aiding in keeping track of the progress of the incidents.

Incident Alert
This module sends notifications for the alerts generated by the Vairav CTMS. By default, the overall notifications are sent to Vairav IR, which can be configured to be sent via email, slack or any other communication platforms along with web hooks.

Reporting
This module generates reports based on pre-defined templates in Vairav CTMS or custom templates that are created as per the customer’s requirements.

Email Breach Detection
This module detects the email addresses whose credentials (username and password) have been compromised already, available publicly on the internet.

File Integrity Monitoring
This module monitors the changes/modification made in specified files and folders within the organization, alongwith the who-data (captures the username as well as the changemaker who is responsible for changes in the monitored files and folders).

Compliance Monitoring
Referred to as the quality assurance test, organizations make the usage of compliance monitoring to acknowledge their business operations, and test whether they meet their regulatory and internal process obligations or not.
Greater ROI
Reduced Risk of Noncompliance
Early Detection of Security Incidents

Greater ROI
Vairav CTMS enables the most effectual use of the security logs and event information, providing solutions and counter-measures, technical support for setup and implementation, insurance protection for data breaches, thereby allowing IT personnel to uncover the full potential of the system.

Reduced Risk of Noncompliance
VAIRAV CTMS effectively monitors the overall information in real-time, flags the unauthorized access to data or information.Consequently, it generates the full report of the logs, taking the needful action when the compliance threshold is passed. Hence, an organization gets ahold of the needful information for the demonstration of compliance or due-diligence during an Audit or investigation.

Early Detection of Security Incidents
VAIRAV provides security analysts with a toolset that enhances their effectiveness. With a proactive security team, a greater likelihood of intercepting and addressing security events in the early stages becomes feasible before impacting the enterprise, therefore reducing the overall information risk profile of the enterprise.

Broader organizational support for Information Security
Vairav comprises a SIEM (Security Incident Management System) involving a broad base of stakeholders working together to evaluate events, create reports and take actions to address the incidents flagged by built-in Vairav CTMS. Eventually, the organizational silos break down, creating a broader and consistent culture of security and overall risk management.

Reduced Operational Costs
Vairav provides the conversion of multiple tools such as SEM, SIM, log management and analysis systems, and database activity monitoring (DAM) into a single solution, enabling the enterprise to save time and money. Moreover, the lessening of the purchase and maintenance costs for proactive monitoring and analysis systems is attainable by a single tool, without compromising its full-fledged functionality.