
Vairav blogs
Blogs



Sep 07, 2020
Snake Ransomware is a Golang ransomware reportedly containing obfuscation not typically seen in Golang ransomware. This malware will remove shadow copies and kill processes related to SCADA/ICS devices, virtual machines, remote management tools, network management software, and others. After this, encryption of files on the device commences, while skipping Windows system folders and various system files. A random 5 character string is appended to encrypted files. According to Bleeping Computer, this ransomware takes an especially long time to encrypt files on a targeted machine. This ransomware is reported to target an entire network, rather than individual workstations.
This blog contains the analysis of snake ransomware. The sample used in analysis was downloaded from https://app.any.run/tasks/7b7d33d9-15f9-4d45-8ae4-291c8cde7ef8/.
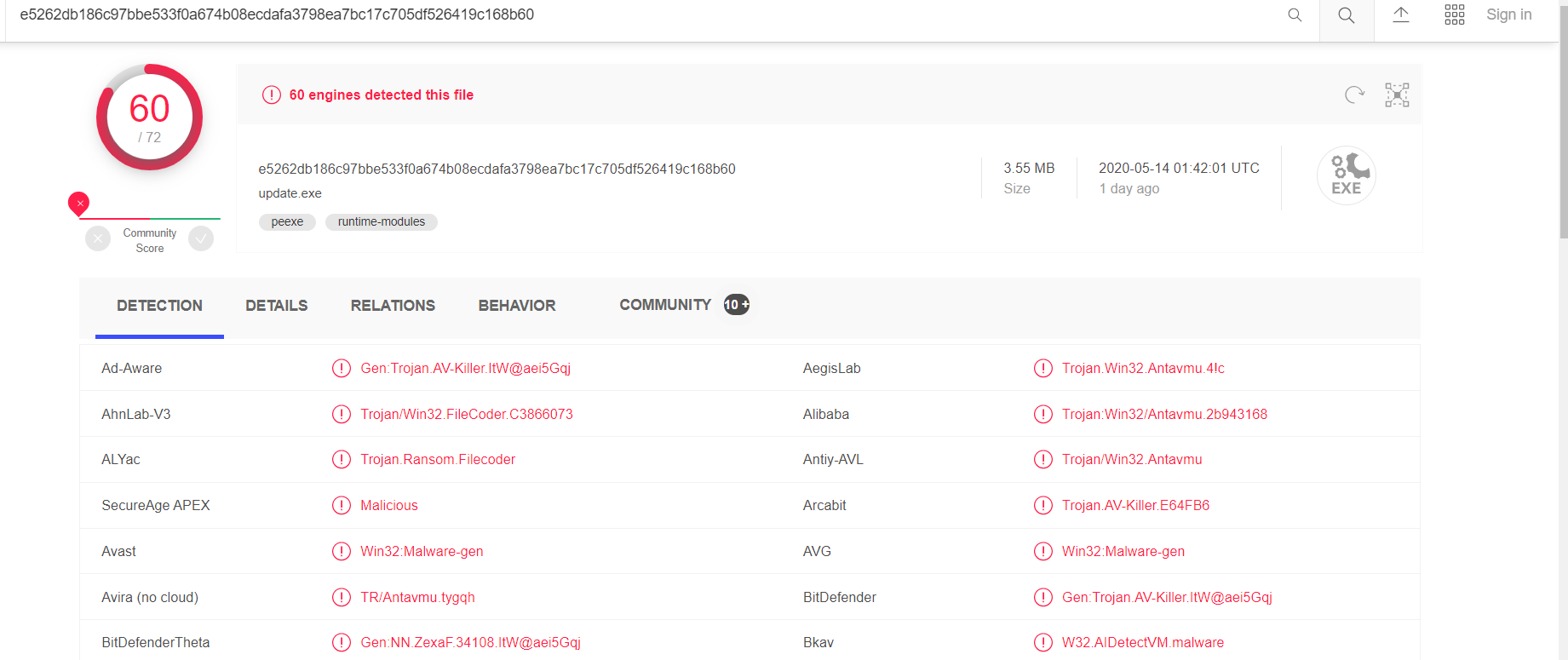
First the sample was submitted to virus total to see if it is identified as malicious https://www.virustotal.com/gui/file/e5262db186c97bbe533f0a674b08ecdafa3798ea7bc17c705df526419c168b60/detection.
virustotal
We can see that 60 out of 72 AV engines detect this sample as malicious.
Using coff explorer tool, we observe that there are very few number of imports, and there is a presence of .symtab section. These both are signs of a binary written and compiled using the GO programming language.
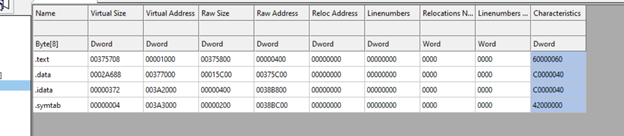

imports
After string analysis, it is confirmed that this is a go binary.

GO build id
Go compiler adds the project used by the malware author

Project Path
Running yara rule in the binary with the rules found in this public repository https://github.com/Yara-Rules/rules we get the following results.

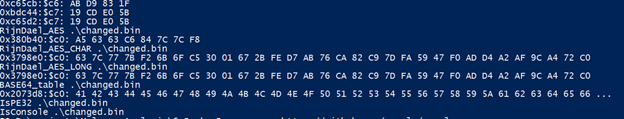
AES encryption data
We can see that the malware has possible CnC traffic, and that malware is capable of performing AES encryption.
For basic dynamic analysis, the malware was already run in app.any.run, so i observed the data from there.

app.any.run sandbox data
The malware is touted as malicious, but i do not see any network connection. So I ran the malware in a VM, the malware encrypted most of the data, but i could not file any help text, as to how to recover them.

Unlike regular golang binaries, there were no regular function names. The malware author has thus attempted to obfuscate the various function names.
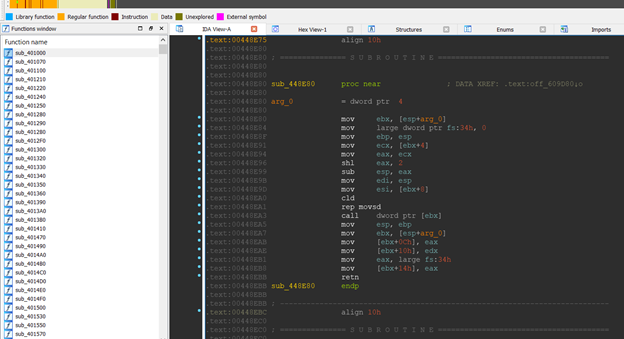
Code Obfuscation
So in order to de-obfuscate the function names a tool called idagolang helper was used https://github.com/sibears/IDAGolangHelper.
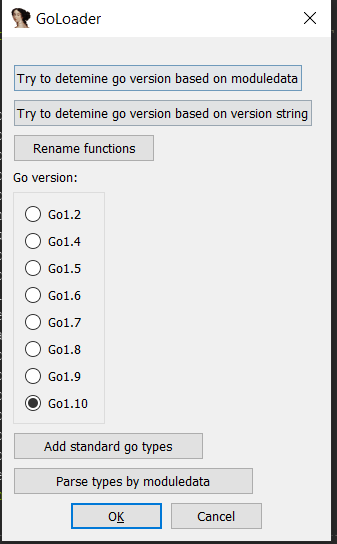
Using IDA Golang Helper tool
Now we are going in a right direction. There are a lot of golang builtin functions that we can see. But looking at function name, I was trying to get a hint of the purpose the various main functions , but the function names itself is weird and was most likely obfuscated/randomized to slow down reversing process.
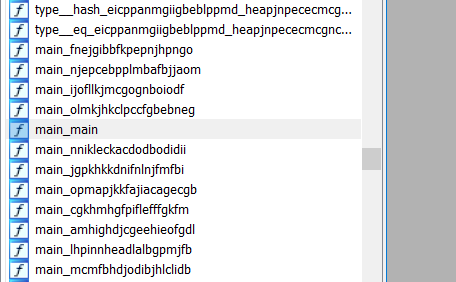
Golang built in functions renamed, but main names are garbage
So I started analyzing the main functions, eventually it led me to the syscall function call from the golangs built in function.
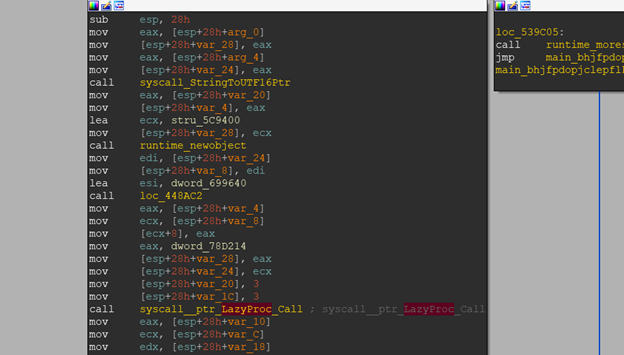
syscall
So after referring to the golang documentation at https://golang.org/pkg/syscall/?GOOS=windows, it seemed that it was used to call a function from a windows dll file. Here’s a snippet.
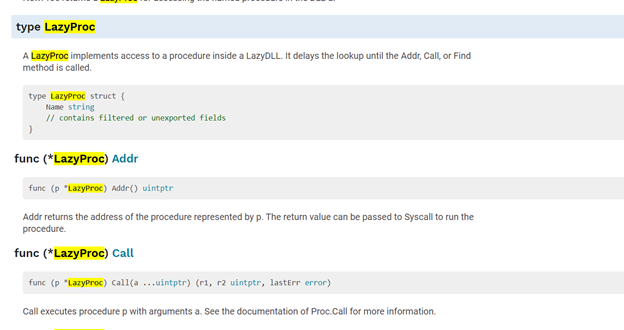
Golang documentation
I could not determine the exact function being called via static analysis, so had to run the sample inside a debugger.
It seems the function that was being called is CreateMutexW.


By observing that the value esp+0x18 being used in error condition check we can assume that it is the lastErr value and the rest is the returned pointer. Looking at this, we can safely assume, that the function main_bhjfpdopjclepflkbeoj is responsible for calling the windows function CreateMutexW and returning its value. Renaming the function to sycall_function. Renamed main_ienocpmdijcihngapkhe to calls_function_Creating_global_and_sycall_create_mutex.
Continuing further analysis, the function at 0054E480 was responsible for key extraction.

Key extraction
I did not see network communication for getting key, and after running the malware multiple times, the key seems to be the same “ — — -BEGIN RSA PUBLIC KEY — — -\nMIIBCgKCAQEAyQ+M5ve829umuy9+BSsUX/krgdF83L3m8/uxRvKX5EZbSh1+buON\nZYr5MjfhrdiOGnrbB1j0Fy31U/uzvWcy7VvK/zcsO/5aAhujhHB/qMAVpZ8zT5BB\nujT1Bvsith/BXgtM99MixD8oZ67VDZaRM9TPE89WuAjnaBZORrk48wFcn1DOAAHD\nZ9z9komtqIH1fm3Y0Q6P76nUscLsYOme082L217Th/lTMoqqs4cF2rn9O9Vp4V9U\naCs4XVxGSpcuqbIscfpf0cm44P2eOEk+sbZdahO9C6fezt7YF4OCJ4Vz3qqMD6z4\n+6d7FRxUu6k3Te2T2bWBZnsDO30pYFi/gwIDAQAB\n — — -END RSA PUBLIC KEY — — -\n”.
After in depth analysis, it seems function with name pattern main_ffhlhdmhalodcojcaeok_*** seems to be junk function, because the function just converts slice of byte to string or vice versa, and the value is not useful at all.
Digging further, function sub_0053A060 is responsible for looping through each files and encrypting them and finally the function main_amgmhoeegchpnnaljano 00539C30 eventually calls io_ioutil_WriteFile. I thought it could be possibly help file, so i debugged it and trying to find what it actually wrote.

Debugging
The file is at C:\\Fix-Your-Files.txt. but I could not find the file. The ransomware seems to have failed to write the file. So i thought may be it needed admin privileges to write the help file. I ran the sample again with admin privileges, and now it has written the file.

Help Message
This just seems extremely odd. I do not understand why the author chose to write the help file in such a specific location where the user had to search for it. Other ransomware seem to have changed the wallpaper itself, or drop the help file in each file. It just seems like a bad choice to keep the help file in a specific location where to write admin privileges was required.
Yara rule for this ransomware:
rule SnakeRansomware{meta:Author = "Nishan Maharjan"Description = "A yara rule to catch snake ransomware"Data = "15th May 2020"strings:$go_build_id = "Go build ID: \"X6lNEpDhc_qgQl56x4du/fgVJOqLlPCCIekQhFnHL/rkxe6tXCg56Ez88otHrz/Y-lXW-OhiIbzg3-ioGRz\""$math_rand_seed_calling = { 89 C8 BB 00 CA 9A 3B 89 D1 F7 E3 81 E1 FF FF FF 3F 89 C3 01 C8 89 C6 05 00 00 1A 3D 89 04 24 69 ED 00 CA 9A 3B 01 EA 89 CD C1 F9 1F 01 EB 11 CA 81 C6 00 00 1A 3D 81 D2 EB 03 B2 A1 89 54 24 04 E8 10 62 F6 FF }$encryption_function = {64 8B 0D 14 00 00 00 8B 89 00 00 00 00 3B 61 08 0F 86 38 01 00 00 83 EC 3C E8 32 1A F3 FF 8D 7C 24 28 89 E6 E8 25 EA F0 FF 8B 44 24 2C 8B 4C 24 28 89 C2 C1 E8 1F C1 E0 1F 85 C0 0F 84 FC 00 00 00 D1 E2 89 CB C1 E9 1F 09 D1 89 DA D1 E3 C1 EB 1F 89 CD D1 E1 09 D9 89 CB 81 C1 80 7F B1 D7 C1 ED 1F 81 C3 80 7F B1 D7 83 D5 0D 89 C8 BB 00 CA 9A 3B 89 D1 F7 E3 81 E1 FF FF FF 3F 89 C3 01 C8 89 C6 05 00 00 1A 3D 89 04 24 69 ED 00 CA 9A 3B 01 EA 89 CD C1 F9 1F 01 EB 11 CA 81 C6 00 00 1A 3D 81 D2 EB 03 B2 A1 89 54 24 04 E8 10 62 F6 FF 31 C0 EB 79 89 44 24 20 8B 4C 24 40 8D 14 C1 8B 1A 89 5C 24 24 8B 52 04 89 54 24 1C C7 04 24 05 00 00 00 E8 48 FE FF FF 8B 44 24 08 8B 4C 24 04 C7 04 24 00 00 00 00 8B 54 24 24 89 54 24 04 8B 5C 24 1C 89 5C 24 08 89 4C 24 0C 89 44 24 10 E8 EC DD EF FF 8B 44 24 18 8B 4C 24 14 89 4C 24 08 89 44 24 0C 8B 44 24 24 89 04 24 8B 44 24 1C 89 44 24 04 E8 68 BB F3 FF 8B 44 24 20 40}condition:all of them}