
Vairav blogs
Blogs



Feb 07, 2022
On Dec 30, 2021, a piece of news circulated regarding a ransom note sent by a cyber criminal’s group (SaudeGroup) through email to the victim organization of Nepal stating that the criminal group has compromised the victim organization IT infrastructure and has erased internal data.
Our Cyber Security Operation Center team created a task force to investigate this security event from our side with hypotheses. We collected the data from Dark Web, previous news, and private telegram channel and constructed the report of this group historical data, the tactics and techniques used, and the remediation to prevent the cyber-attacks from such group.
“SaudeGroup”, primarily known as Lapsus$ group is a Brazilian Portuguese native speaker ransomware group. This group targets the organization for ransom by compromising the public-facing applications and misconfigured AWS infrastructure. This group is a new ransomware group that was previously involved in leaking EA data containing FIFA 21 source code.
Cyber Criminal Group Name: Lapsus$ Group aka SaudeGroup
Criminal Characteristic: Ransomware Gang
Country of Origin: Brazil
Active Since: July 2021
Email Address: saudegroup@ctemplar.com
Telegram Channel: https://t.me/minsaudebr, https://t.me/saudechat
Most Targeted System:
This group mostly targets the government and private organizations of Brazil. Previously this group has compromised the infrastructure of Ministry of Health, Brazil. And recently it has hacked SIC, Portugal’s largest TV channel and Brazilian company Claro, NET and Embratel systems.
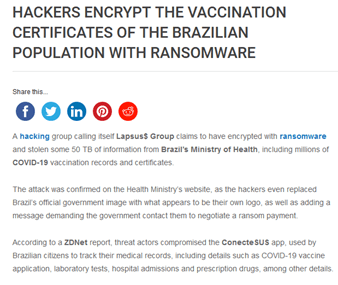
LAPSUS$ Group deletes all the data of the compromised system and demands a ransom to return the deleted data and if their demand is not fulfilled then they will release the data on the internet.
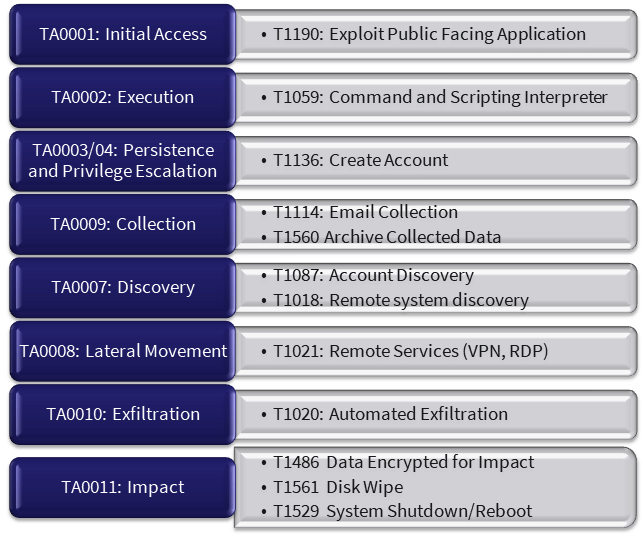
Lapsus$ Group begins its cyber-attack campaign by scanning targets public-facing applications for the vulnerability. This group mainly targets Microsoft Exchange Server, FortiGate Firewall, and public AWS infrastructure. Our Threat Intelligence team has already identified that more than a dozen of Grade A Banks, Life Insurance, Finance, Luxury Resort, Digital Financial Service Provider, and Government Agency is vulnerable to CVE-2021-34473, CVE-2021-26858, CVE-2021-26857, CVE-2021-26855, CVE-2021-31207, CVE-2018-13379, CVE-2020-12812, CVE-2019-5591, and the vulnerable system is still not patched.
This group exploits the vulnerable Microsoft Exchange Server and FortiGate firewall to get access to the victim internal network and after getting internal access, they create a bogus account to maintain persistence, and the same user account is used to escalate the privilege to super admin of the compromised Microsoft Exchange Server and FortiGate firewall.
After getting a hold of super admin privilege, the criminal group starts to collect the internal systems and user credentials. They too start to collect the inventory of internal critical applications and systems with respected system user credentials. The collected critical application details and user credentials are used by criminals to exfiltrate the internal data and whenever the exfiltration task is done, they delete the whole server environment to demand the ransom. We have found that the LASPUS$ group targets internal systems like vCenter, VMware vSphere, Veeam Backup & Replication, etc.
LAPSUS$ Group uses the “Mole Hiring” tactics to infiltrate the victim organization digital infrastructure. They look for the VPN/Remote Desktop user credentials.