
Vairav blogs
Blogs



Feb 06, 2022
Ransomware has been around for decades now; it has gained significant popularity among cyber criminals. The emergence of cryptocurrency, which permits near-anonymous payments, widespread digitization of sensitive data, and the release of sophisticated ransomware-as-a-service criminal business models are all contributing to this growth. Ransomware works by encrypting the victim’s corporation data and making it unusable. After starting the attack, cyber criminals would offer to sell the victim a decryption key. If the victim refuses, they must accept the catastrophic loss of their most sensitive information. A two-pronged method is used by some ransomware attacks. For decrypting data, attackers will demand a ransom payment and threaten to publicly reveal critical information if the ransom is not paid by a particular date. (“Double Extortion”)
This article focuses on a group called “Conti,” which seems to be the same as “Wizard Spider.”
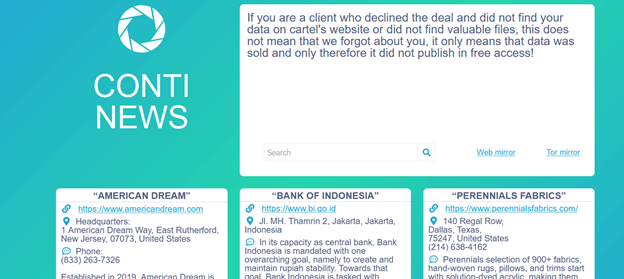
CONTI is a ransomware group that forces victims to pay the ransom via a double extortion approach. In other phrases, the attackers will not only encrypt a victim’s data and demand a ransom to decode them, but they will also steal them and threaten to publish them on a website or otherwise leak them if the ransom is not paid. Conti scans networks for priority targets, spreads throughout the network, then encrypts every device and account it finds. Conti employs a ransomware-as-a-service (RaaS) model.
Conti is a ransomware-as-a-service (RaaS) affiliate program linked to Russian-speaking cyber criminals that was first discovered in early 2020. Until early 2020, the group did not have its own website.
Ransomware has been around for decades now; it has gained significant popularity among cyber criminals. The emergence of cryptocurrency, which permits near-anonymous payments, widespread digitization of sensitive data, and the release of sophisticated ransomware-as-a-service criminal business models are all contributing to this growth. Ransomware works by encrypting the victim’s corporation data and making it unusable. After starting the attack, cyber criminals would offer to sell the victim a decryption key. If the victim refuses, they must accept the catastrophic loss of their most sensitive information. A two-pronged method is used by some ransomware attacks. For decrypting data, attackers will demand a ransom payment and threaten to publicly reveal critical information if the ransom is not paid by a particular date. (“Double Extortion”)
This article focuses on a group called “Conti,” which seems to be the same as “Wizard Spider.”
CONTI is a ransomware group that forces victims to pay the ransom via a double extortion approach. In other phrases, the attackers will not only encrypt a victim’s data and demand a ransom to decode them, but they will also steal them and threaten to publish them on a website or otherwise leak them if the ransom is not paid. Conti scans networks for priority targets, spreads throughout the network, then encrypts every device and account it finds. Conti employs a ransomware-as-a-service (RaaS) model.
Conti is a ransomware-as-a-service (RaaS) affiliate program linked to Russian-speaking cyber criminals that was first discovered in early 2020. Until early 2020, the group did not have its own website.
| Initial Access | Phishing (T1566) Conti primary means of infection appears to be through phishing scams Exploit public-facing application (T1190) Conti can be delivered by exploiting the FortiGate firewall vulnerabilities CVE-2018-13379 and CVE-2018-13374.Conti potentially appears because of the ProxyShell Microsoft Exchange vulnerabilities being exploited. |
| Execution | Execution through API (T1106) Conti uses the Native API to do tasks like erasing shadow copies. Command and scripting interpreter: Windows command shell (T1059.003) Conti distributes and executes malware using batch files. Once within the network, the actors typically employ scheduled tasks and batch files to execute commands on remote devices.Alternatively, the ransomware can be executed using files such as the DontSleep.exe process, which invokes the task manager and executes the file. Windows Management Instrumentation (T1047). Conti leverages Windows Management Instrumentation (WMI) to run batch scripts and remove shadow copies. User execution (T1204) The payload from the spear phishing link requires user execution. |
| Persistence | Scheduled task/job: scheduled task (T1053.005) Conti uses scheduled tasks as a method of ransomware execution. |
| Privilege Escalation | Valid accounts: domain accounts (T1078.002) Conti elevates privileges in the system by using domain administrator accounts.Although the group primarily relies on obtaining domain admin credentials to get full access to the domain, they may also employ exploits such as Zerologon (CVE-2020-1472) and PrintNightmare (CVE-2021-1675) to escalate their privilege and further strengthen their network foothold. File and directory discovery (T1083) Conti Looks for specified files and directories associated with the encryption.Considering the fact the Conti use double extortion, they actively seek out files to exfiltrate during the discovery stage. Threat actors use tools like ShareFinder to find the shares they need for data exfiltration and ransomware distribution. Remote system discovery (T1018) To enable distribution to remote systems, Conti enumerates ARP entries. Process discovery (T1057) Conti determines which processes should be terminated. System network configuration discovery (T1016) The Conti group uses tools like Whoami, Nltest, and Net for early reconnaissance. These tools notify operators about where they are in the system, as well as their rights and permissions. Permission groups discovery: domain groups (T1069.002) Conti looks for group information in order to escalate privileges. System information discovery (T1082) Conti collects data from system data in order to keep track of the system. System owner/user discovery (T1033) Conti performs System owner/user discovery to escalate privilege. Query registry (T1012) Conti scans a registry for passwords that have been saved. Security software discovery (T1063) Conti discovers security software that can be used for reconnaissance and termination. |
| Credential Access | OS credential dumping (T1003) Conti dumps LSASS memory to be used for password hashes retrieval.For lateral movement or to enhance their privilege, the Conti dump cached credentials on systems. They dump system processes (typically lssas.exe) using tools like ProcDump, which they combine with Mimikatz to dump credentials. Credentials from password stores (T1555) Conti uses tools like SharpChrome and net-GPPP to retrieve passwords from credential stores. Unsecured credentials (T1552) Conti uses Mimikatz to retrieve credentials.Conti may also use the PowerShell empire’s kerberoasting module or other tools like Rubeus. |
| Lateral Movement | Lateral tool transfer (T1570) Conti uses BITSadmin to transfer tools across the network. Remote services: SMB/Windows admin shares (T1021.002) Conti has also been known to use EternalBlue to move laterally in a network of vulnerable systems.Conti Ransomware spreads via SMB and encrypts files across multiple systems, posing a threat to an entire network. |
| Defense Evasion | Impair defenses: disable or modify tools (T1562.001) Conti creates a series of batch files just before the ransomware executes to automate the distribution of their tools in the domain. Scripts to stop existing security software are included with these tools.Conti may also use other tools to accomplish this, such as GMER, PC Hunter, and PowerShell. Deobfuscate/Decode files or information (T1140) Conti Obfuscate to make detection more difficult Process injection (T1055) Conti uses a Process Injection technique to make detection more difficult.Conti ransomware loads and runs an encrypted dynamic-link library (DLL) into memory. |
| Command and Control | Application Layer Protocol (T1071) Conti Uses HTTP protocol to communicate with CnC server. Remote access software (T1219) Conti makes use of RMM tools like AnyDesk and Atera. |
| Exfiltration | Exfiltration over web service: exfiltration to cloud storage (T1567.002) Conti syncs files with a cloud storage account, such as Mega.Conti uses the Rclone tool, which is an open-source application for syncing files to a chosen cloud storage, such as Mega cloud storage, to exfiltrate data from the system.Conti can also exfiltrate data via WinSCP. |
| Impact | Data encrypted for impact (T1486) The files are now encrypted using ChaCha20 with RSA4096 to protect the ChaCha key and nonce, after exfiltration and distribution of the ransomware to the targeted endpoints. Service stop (T1489) Conti employs tools like PC Hunter and GMER to shut down security-related services. Inhibit system recovery (T1490) Conti Uses Wmic to delete Shadow copies. |
In August 2021, Angry Conti ransomware affiliate leaked the gang’s attack playbook as he was paid comparatively less. The malware tools and exploits listed below are commonly utilized in conti ransomware attacks.
| Execution | Bazar Loader, Cobalt Strike, Emotet, IcedID |
| Discovery | Adfine, netscan, Nltest, Sharefinder, SharpView, whoami |
| Privilege Escalation | Eternal Blue, Mimikatz, Routerscan |
| Credential Access | Mimikatz, Net-GPPPassword, ProcDump, Rubeus, RouterScan, Vssadmin, SMB AutoBrute |
| Lateral Movement | Anydesk, Atera, BITSAdmin, Cobalt Strike, EternalBlue, Mimikatz, PsExec |
| Defense Evasion | GMER, prockiller, PCHunter |
| Exfiltration | Winscp |
| Command and Control | Anydesk, Atera, CobaltStirke |
We recommend organizations to implement a cyber defense layer, implement proper vulnerability management programs and enforce continuous Security Monitoring to neutralize cyber-attacks.
Author: Nischal Khadgi, Cyber Threat Intelligence Analyst