
Vairav blogs
Blogs



Nov 25, 2020
Vairav Security Analyst has discovered 49,577 IP addresses vulnerable to fortinet ssl vpn (cve-2018-13379) from around the world which was shared publicly on the dark web. The Fortinet VPN devices included in the list are vulnerable to the CVE-2018-13379, which is a path traversal vulnerability in the FortiOS SSL VPN web portal that could be exploited by an unauthenticated attacker to download FortiOS system files, to upload malicious files on unpatched systems, and take over Fortinet VPN servers. The vulnerability was officially patched by Fortinet in April and May of 2019.
This leak was made public on November 18, 2020 by user mont4na (previously known as ‘pumpedkicks’).
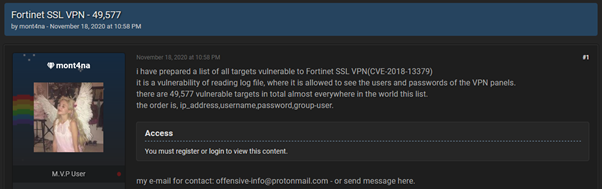
First announcement of vulnerable IP Addresses
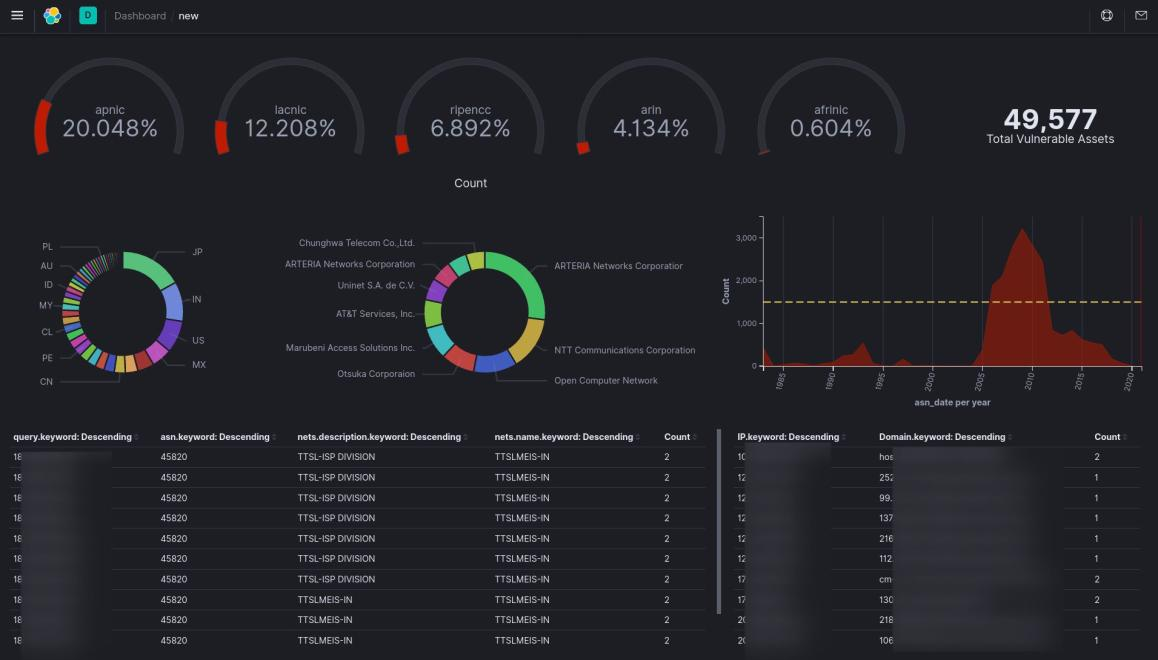
Visualization of Vulnerable IP Addresses
The total 219 countries were affected in this list standing USA, Japan and India at the top. Significant percent of countries from Asia-Pacific region were affected while the TLDs belong to all types including government and financial domains.
.png)
Top victim Countries
Our Analyst has also identified 49 IP addresses belonging to various organizations from Nepal which were included in the leak.
.png)
Top Affected assets as per the ISP
The actor seems to be active in the dark market. The link to the leak was found dead a few days after this news was covered but the new thread regarding the same leak has been made public with a different account with the clear text password of vulnerable assets. The leak has been shared and talked over several underground forums and chat hinting for the major cyber attack (data breach, Ransomware) in the near future.
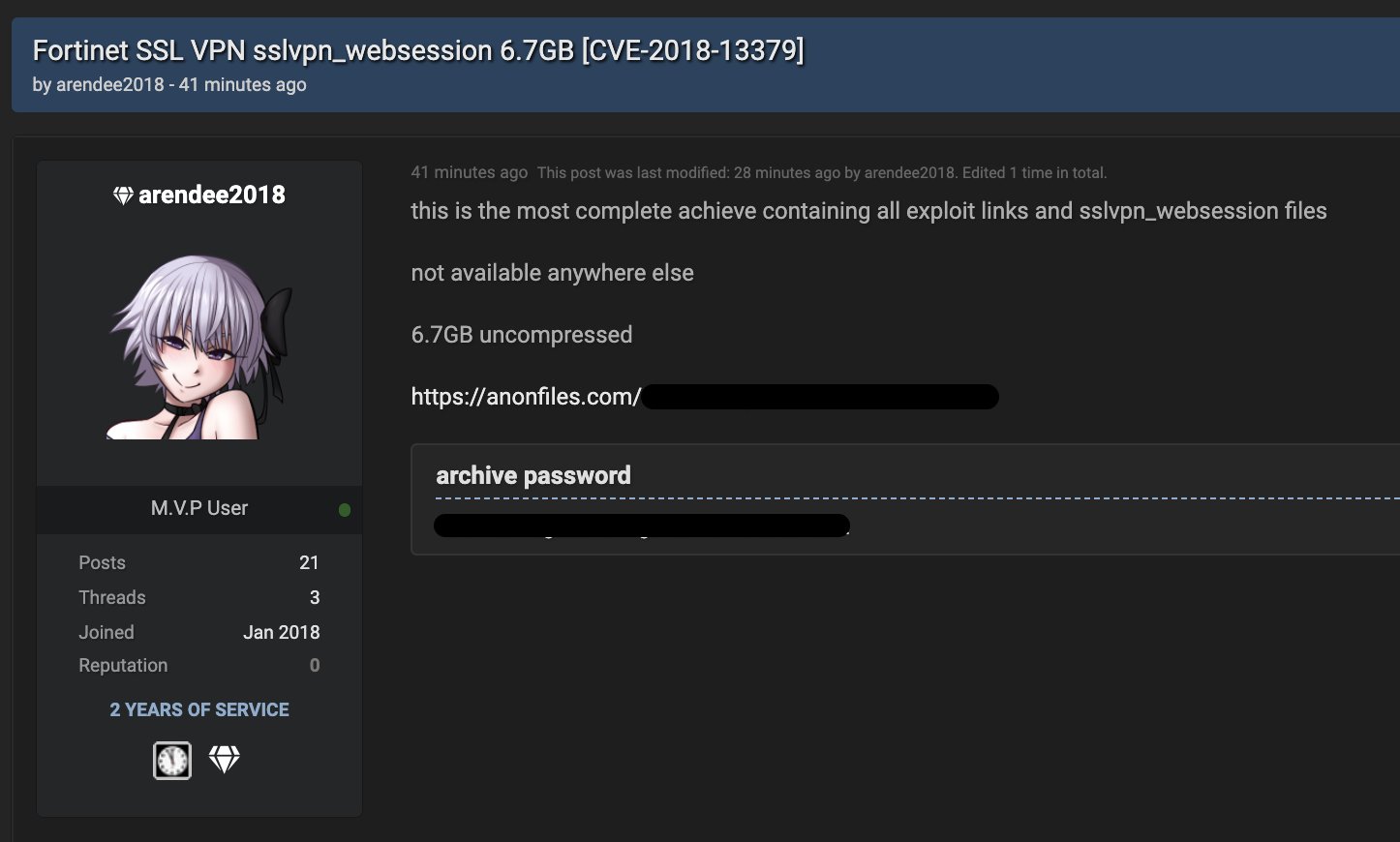
Thread exposing credentials in clear text
.png)
The same leak data were shared in Russian speaking hacker forum.
.png)
Snippet of leaked VPN credentials
The most worrisome aspect of this discovery is that despite the CVE-2018-13379 is a well-know vulnerability, many organization have yet to fix it more than 2 years after its public disclosure.
Finally, this leads to the possibility of vulnerable assets getting misused and attackers could use them to gain access to the target networks and carry out multiple malicious operations, such as manually delivering malware and ransomware.